Hire Developers With Cybersecurity Compliance Software Development Experience
For the healthcare, accounting, payment/banking, and other industries, our software engineers have years of practical expertise designing, creating, and developing cybersecurity compliant software solutions.
Unique Threat Prevention Strategies
Our AI-driven solutions provide IOA/IOC and HIPS/HIDS capabilities to detect covert malware, and are designed to detect threats using cutting-edge machine learning algorithms.

Privileged Access Management (PAM)
PAM capabilities make it simple to control user permissions, enhancing endpoint security with simple governance.
DNS, HTTP, & HTTPS Filtering
A cutting-edge set of tools for filtering DNS, HTTP, and HTTPS traffic that uses machine learning techniques to stop online threats.
Patch Management
With the help of cybersecurity compliance solutions, you can efficiently deploy, patch, and manage your software inventory on a single platform.
Security Compliance Software Development
We create security compliance software that complies with several security compliance standards, including PCI, HIPAA, HITECH, GDPR, FISMA, ISO 27000, SEC, GLBA, FINRA, NYDFS, and NIST 800-171.
Cyber Compliance Management
Solutions for managing and monitoring compliance with a variety of IT rules and standards are available to businesses.
Business Continuity Management
Cybersecurity solutions to monitor and execute business continuity can track disasters, recover programs, do risk assessments, and more.
Cyber Vendor Risk Management
Software for cybersecurity compliance to discover, evaluate, manage, and track various risks associated with IT vendors to improve and hasten well-informed decision-making.
Identity & Access Management
Enable embedded credential management by implementing enterprise single sign-on (ESSO), multi-factor authentication (MFA), role-based access controls (RBAC), and other enterprise-level identity and assessment management (IAM) protocols.
Cyber Governance, Risk, & Compliance
The HIPAA, PCI DSS, SAS 70, and other standards governing healthcare, payments, and accounting are just a few of the industries that cyber risk management solutions are meant to comply with.
Cybersecurity Application Development
When developing our custom mobile and online applications, run enterprise-wide dynamic application security tests (DASC) to check for effective security standards of business logic, stealth code (malware, hidden sites, backdoors, etc.), and more.
Cyber & IT Infrastructure Security
File integrity monitoring, firewall auditing, next-generation firewall (NGFW) implementations, intrusion detection and prevention systems (IDS/IPS), and advanced persistent threat (APT) security are all included into solutions.
Advanced Firewall & Antivirus Protection For Business Networks
We create thorough firewall and antivirus solutions that protect your systems from the most recent viruses, malware, spyware, ransomware, and other assaults.
Man-in-the-Middle (MitM) Attacks
Our real-time suspicious activity monitoring, IP address/firewall blocking, and multiprotocol message decoding cybersecurity techniques will help you avoid MitM attacks.
DDoS Attacks, Ransomware, & Phishing
Protect critical company data from theft by defending against DDoS attacks, ransomware attacks, ethical hacking, phishing, and other breaches.
VLAN Hopping Attacks
Configure and implement VLAN trunks to protect your web traffic, network credentials, employee information, and other crucial data against switch spoofing and double tagging.
Data Backup & Recovery Services
We create thorough firewall and antivirus solutions that protect your systems from the most recent viruses, malware, spyware, ransomware, and other assaults.For a range of enterprise infrastructures, we provide quick, simple, and dependable data backup and recovery services, assuring strong, scalable, and diligently maintained data safeguards.
Data Protection
We create cutting-edge multi-cloud data protection solutions to safeguard your information across a wide range of workload ecosystems.
VMware Integration
We connect VMware with your existing systems to guarantee adaptable and consistent data protection across applications and other VM container settings.
Cyber Recovery
Our software tools for data backup and recovery perform automated data recovery, shielding crucial data from hacker attacks and ransomware.
Remote Workforce Network Security Protection
We put advanced security measures in place on networks that need remote access to ensure the integrity and protection of business data everywhere.
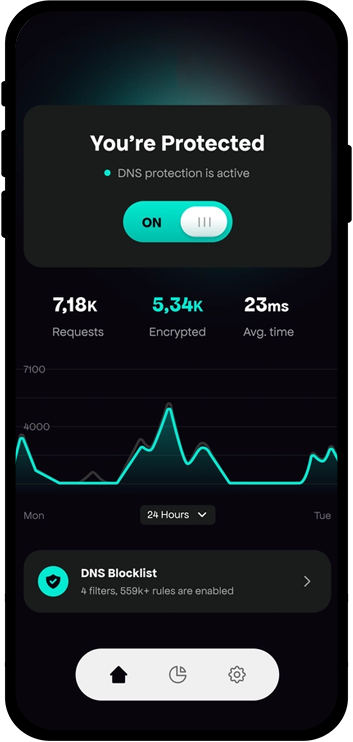
Secure Remote Connectivity
A VPN with integrated two-factor authentication, OTP, smart cards, USB tokens, and other features, as well as SSL or IPsec to secure communications from the devices used by remote workers.
Mobile Device Management (MDM)
Manage everyone who has access to your company's network, their methods of access, and their activities therein.
Container-Specific Security
Containerization protects container contents, reducing data exposure and prohibiting access to crucial data from separate containers both internally and outside.
Custom Cybersecurity Software Solutions
We improve the usability, interoperability, and flexibility of your current cybersecurity solutions by incorporating configurable features, functions, and capabilities.
Cybersecurity Software Solutions
Software solutions for cybersecurity compliance offer a complete 360-degree picture of IT risk management and incident response strategies to get rid of cyber threats.
Threat Intelligence
Solutions analyze your network's weaknesses and fortify the points where your systems are most vulnerable in order to appropriately assess future IT attacks.
Penetration Testing
Throughout the development lifecycle, do proactive penetration testing to find configuration mistakes, software defects, and backdoors that hackers could use.
Data Breach Response
For quicker response times, enable notification and alert settings to alert administrators whenever an internal or external event has occurred.
Cybersecurity Testing Solutions
Before conducting a pen test, implement system-wide backup and disaster recovery solutions to guarantee your regulatory compliance integrity during these simulations.
Ethical Hacking Solutions
Conduct internal system audits and pen-tests to verify data integrity, and map your network to find, exploit, and remove ethical hacking threats.
Security Device Management Solutions
To ensure that your security systems are well-protected against internal and external digital threats, you should design new security device solutions and modify your current security systems.
Data Compliance & Privacy Solutions
Ascertain that all data privacy rules and regulations, such as the GDPR, CCPA, SOC 2 with Privacy, HIPAA Privacy Rule, and others, are fully complied with by your cybersecurity systems.
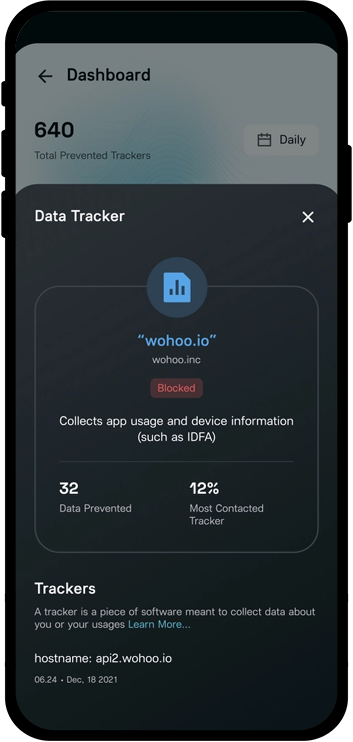
Custom Cybersecurity Software SolutionsCybersecurity Software Third-Party Integrations
We interface with the top cybersecurity compliance software APIs in the market to synchronize your security, defend against threats, and give results that are successdriven.

RSA
In order to quickly link security incidents with business context and help you respond to threats faster, we integrate RSA products with your current business processes.

Sophos
To provide exploit prevention, EDR, ransomware protection, and deep learning malware protection in a single solution, we integrate Sophos endpoint security solutions with your systems.

Cisco
To create a cybersecurity platform that provides simplicity, visibility, and effectiveness across your entire security infrastructure, we leverage Cisco Secure's capability.
SolarWinds
To defend against known dangers, respond rapidly to emerging threats, and easily recover data from disasters, we integrate SolarWinds with government agency systems.
SiteLock
We integrate SiteLock with your systems to decrease the time required for PCI compliance, immediately detect attacks, and secure your data on a single, centralized platform.

Heimdal CORP
By combining local and cloud filtering, we use Heimdal CORP cybersecurity solutions to give your company improved data safety.

Norton
To improve MDM protection for desktop and mobile devices, we deploy cloud-based Norton security software within the already-existing company systems.

Malwarebytes
To stop malware and ransomware attacks, we use Malwarebytes, which provides endpoint security, next-generation threat intelligence, and seamless integrations.
