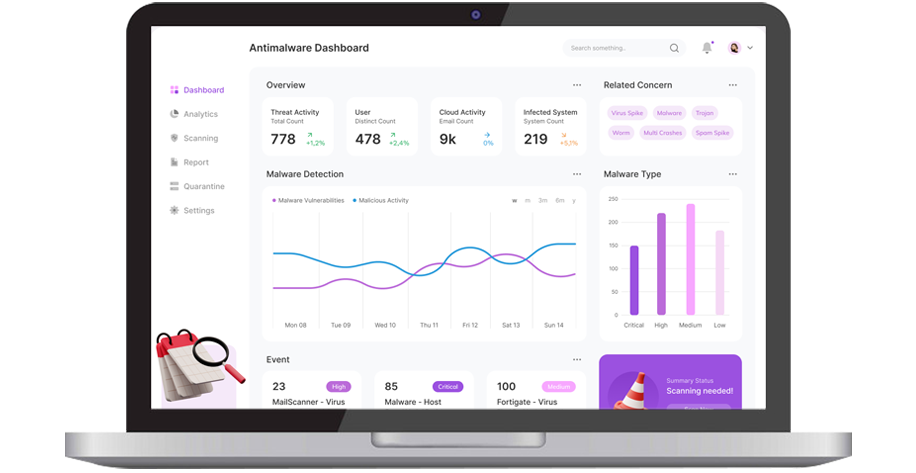
Secure Remote Connectivity
A VPN with integrated two-factor authentication, OTP, smart cards, USB tokens, and other features, as well as SSL or IPsec to secure communications from the devices used by remote workers.
Mobile Device Management (MDM)
Manage everyone who has access to your company's network, their methods of access, and their activities therein
Container-Specific Security
Containerization protects container contents, reducing data exposure and prohibiting access to crucial data from separate containers both internally and outside.